AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
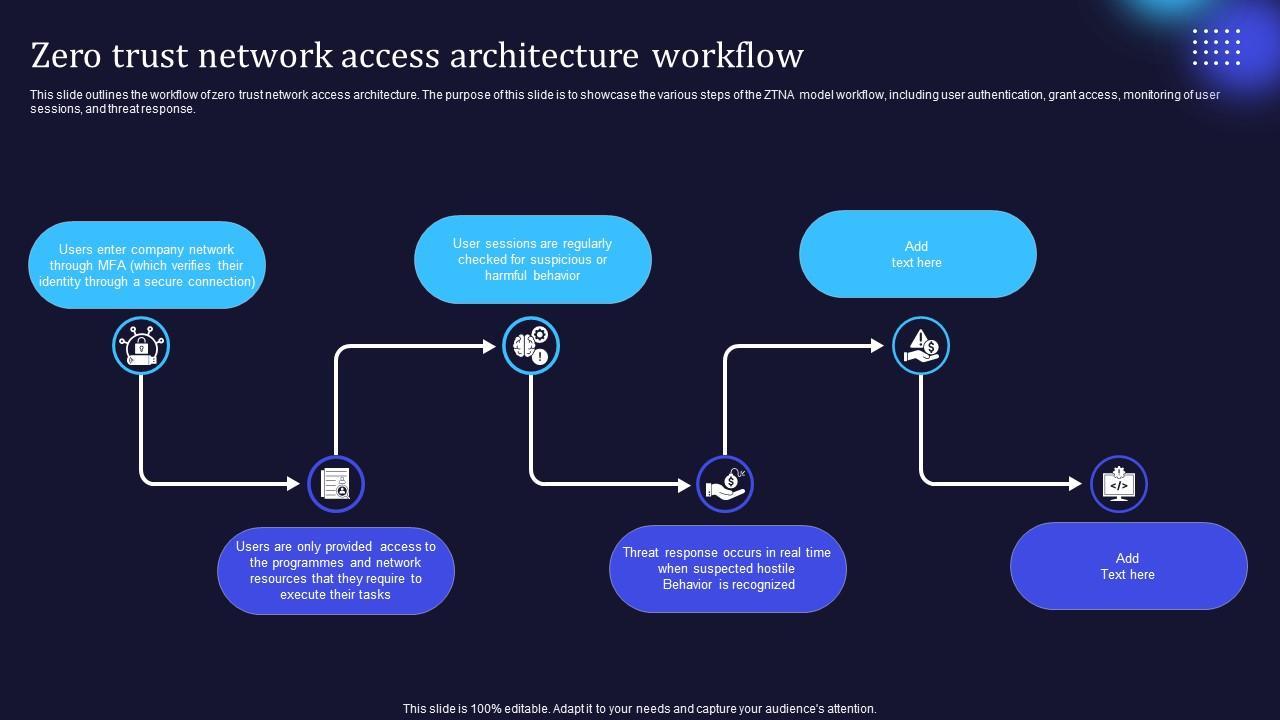
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
Features of these PowerPoint presentation slides:
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Ratings and Reviews
4.5
- ★52
- ★42
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by Garcia Ortiz
May 31, 2024
Good research work and creative work done on every template.by Daryl Silva
May 31, 2024
Design layout is very impressive.by Deshawn Schmidt
May 29, 2024
Best Representation of topics, really appreciable.by O'Kelly Phillips
May 29, 2024
Very unique and reliable designs.
View per page:
10