AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
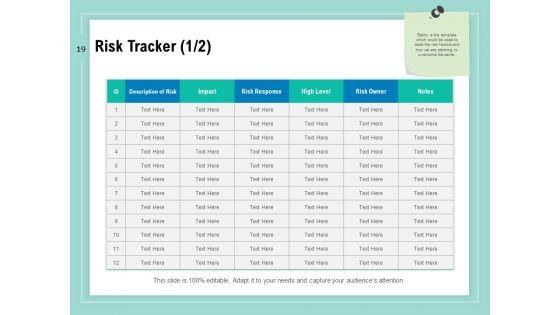
Dashboards
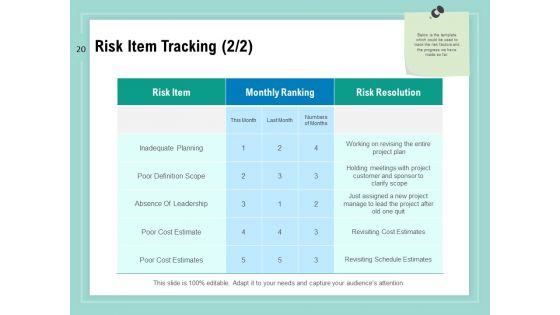
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
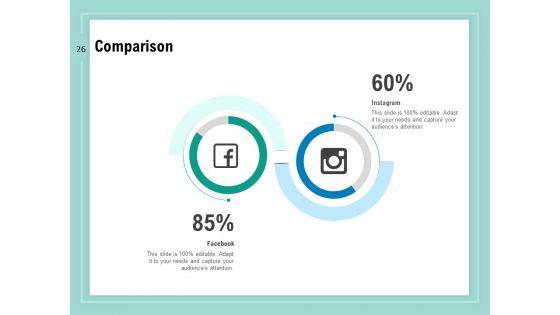
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Vulnerability PowerPoint Presentation Templates and Google Slides
DISPLAYING: 60 of 374 Item(s)
Page
















































Slide 1 of 70
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of seventy slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.












































Slide 1 of 61
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty one slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.







































Slide 1 of 41
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

































Slide 1 of 41
Pitch yourself both in house and outside by utilizing this complete deck. This company vulnerability administration ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fortyone slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

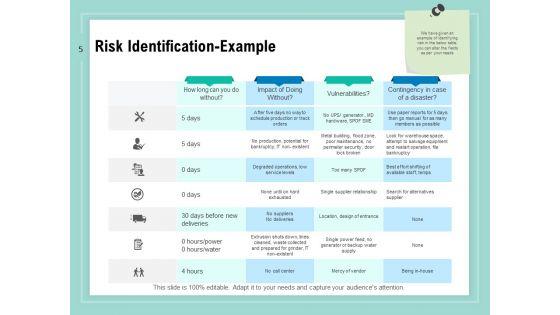
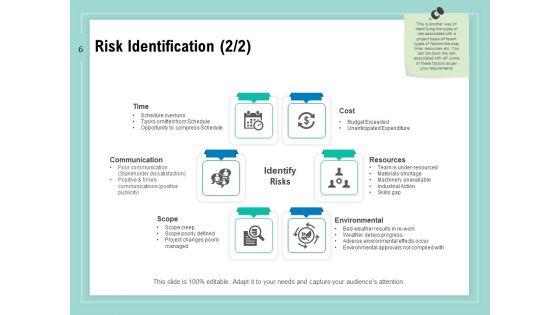

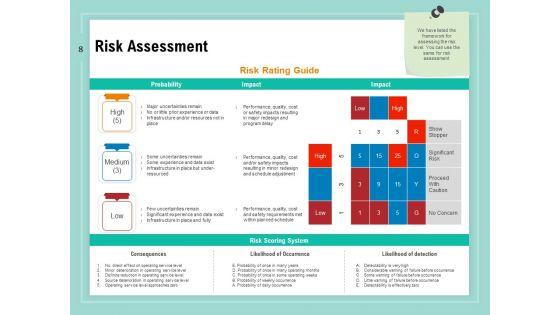
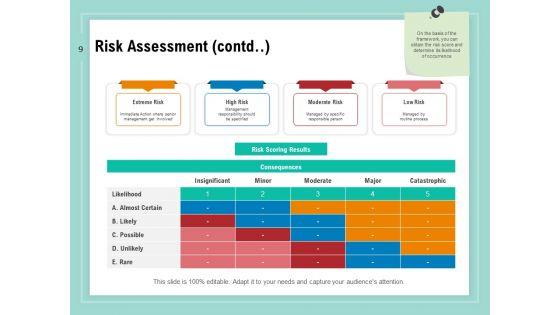
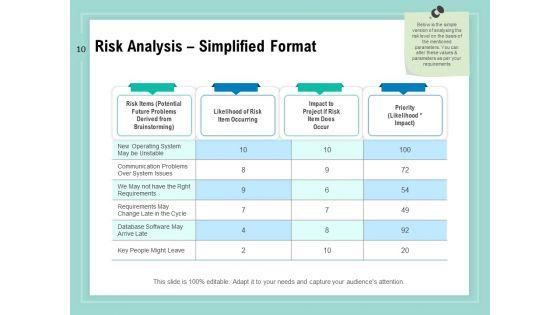
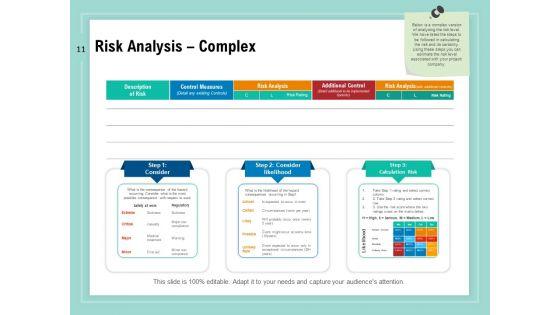

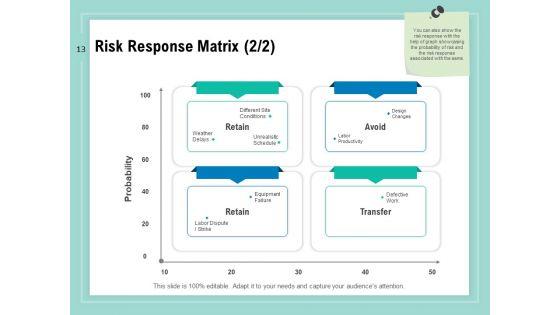
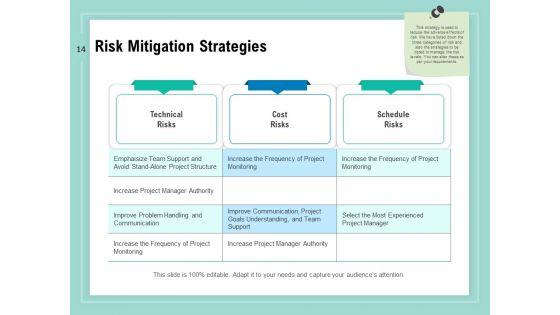
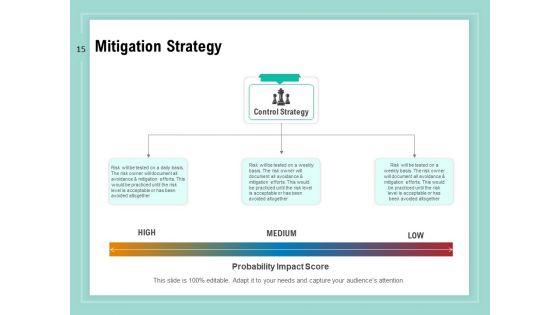
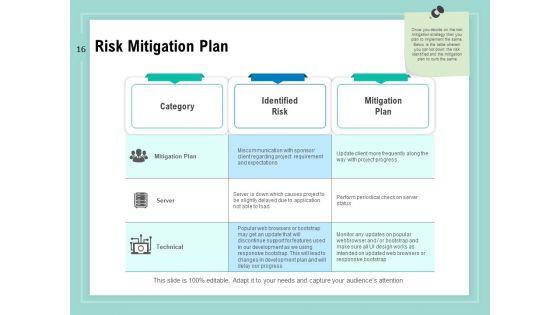
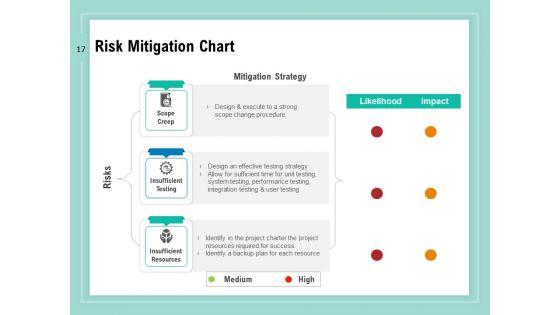
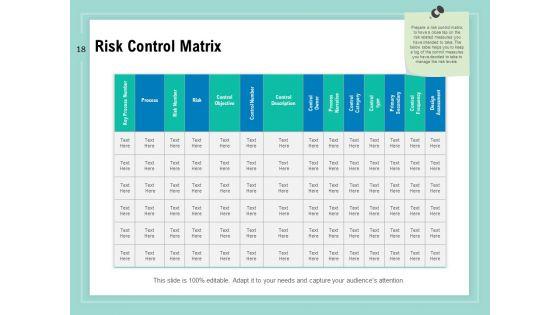




Slide 1 of 34
Presenting this set of slides with name vulnerability assessment methodology ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are analysis, assessment, management, matrix, strategies. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.










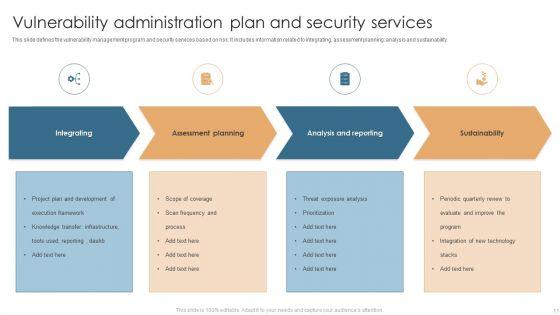
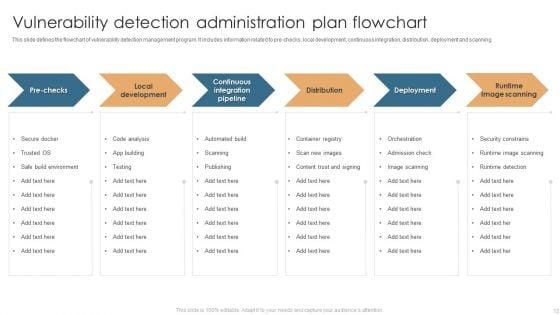
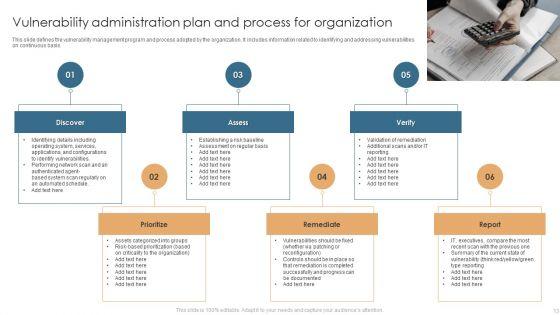



Slide 1 of 17
This Vulnerability Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Vulnerability Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.
Slide 1 of 12
This vulnerability icon weakness supply chain ppt powerpoint presentation complete deck acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this vulnerability icon weakness supply chain ppt powerpoint presentation complete deck PPT slideshow.
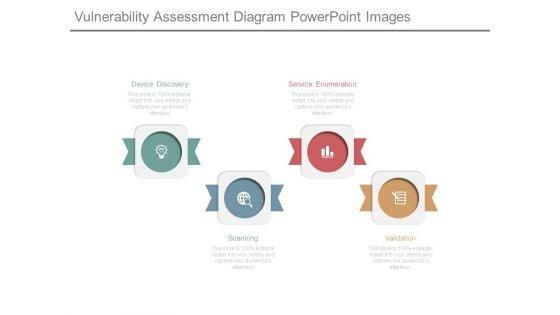

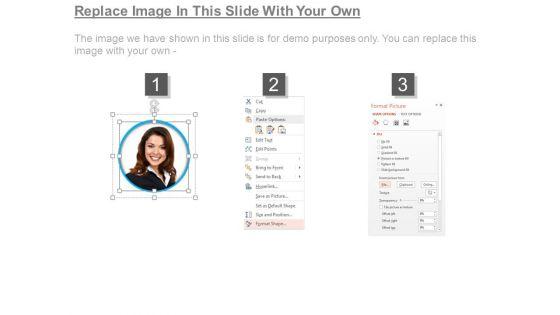
Slide 1 of 7
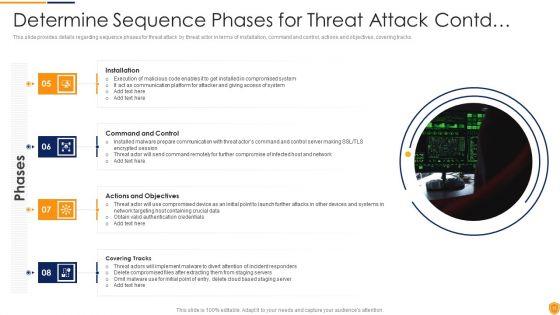
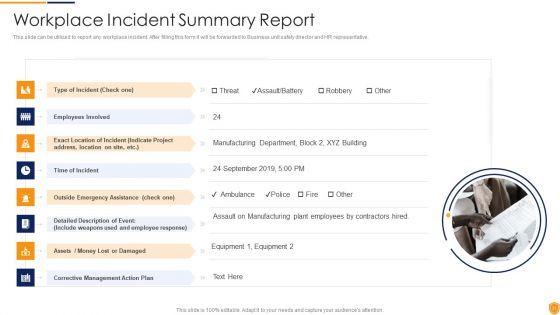
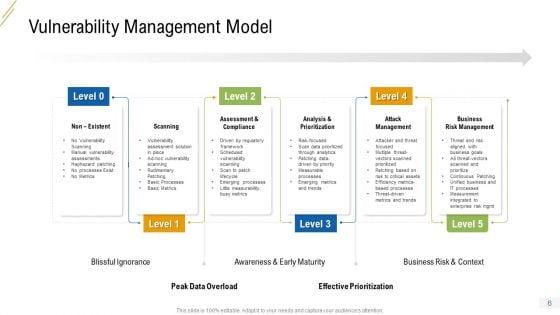
This is a vulnerability assessment diagram powerpoint images. This is a four stage process. The stages in this process are device discovery, scanning, service enumeration, validation.
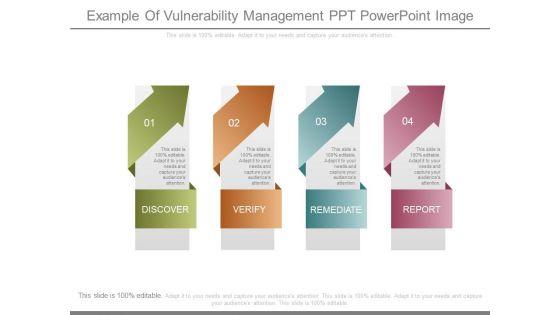


Slide 1 of 7
This is a example of vulnerability management ppt powerpoint image. This is a four stage process. The stages in this process are discover, verify, remediate, report.

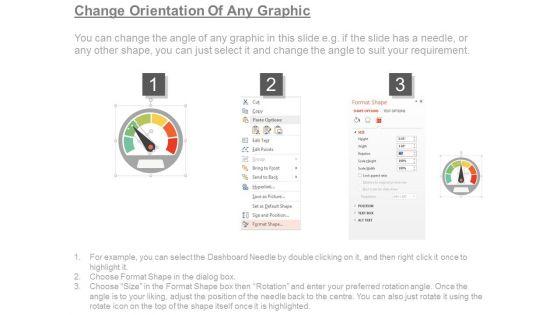
Slide 1 of 7
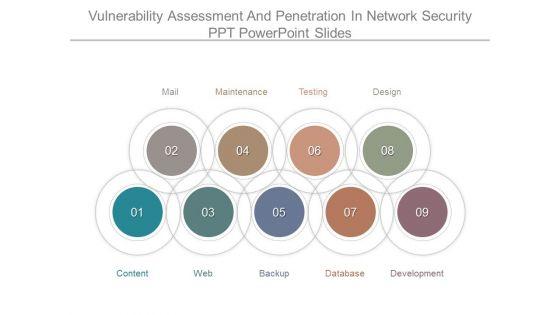
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
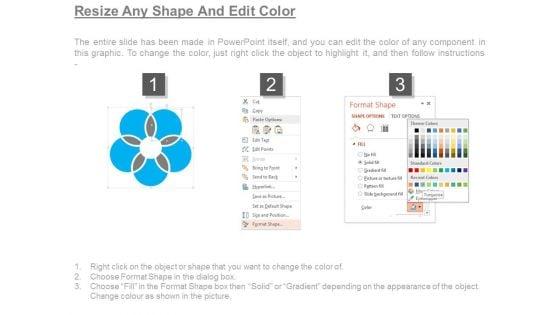

Slide 1 of 7
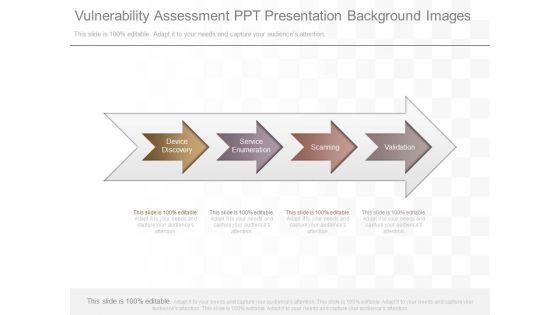
This is a vulnerability assessment ppt presentation background images. This is a four stage process. The stages in this process are device discovery, service enumeration, service enumeration, validation.


Slide 1 of 5
This is a vulnerability assessment companies ppt powerpoint presentation outline graphics design cpb. This is a five stage process. The stages in this process are vulnerability assessment companies.





Slide 1 of 5
This is a network patching and vulnerability management ppt powerpoint presentation ideas themes. This is a five stage process. The stages in this process are patch management process, patch management procedure, patch management approach.



Slide 1 of 5
This is a enterprise vulnerability assessment ppt powerpoint presentation layouts graphics template cpb. This is a one stage process. The stages in this process are enterprise vulnerability assessment.
Slide 1 of 5
This is a vulnerability management process business accounting venture capital availability ppt powerpoint presentation icon graphics. This is a two stage process. The stages in this process are vulnerability management process, business accounting, venture capital availability.





Slide 1 of 5
This is a vulnerability management policy statement production execution business intelligence ppt powerpoint presentation inspiration template. This is a four stage process. The stages in this process are vulnerability management policy statement, production execution, business intelligence.



Slide 1 of 5
This is a project development business operations customer relations vulnerability risk ppt powerpoint presentation infographic template professional. This is a six stage process. The stages in this process are project development, business operations customer relations, vulnerability risk.





Slide 1 of 5
This is a human resources development enterprise vulnerability management 5s manufacturing ppt powerpoint presentation professional microsoft. This is a five stage process. The stages in this process are human resources development, enterprise vulnerability management, 5s manufacturing.


Slide 1 of 2
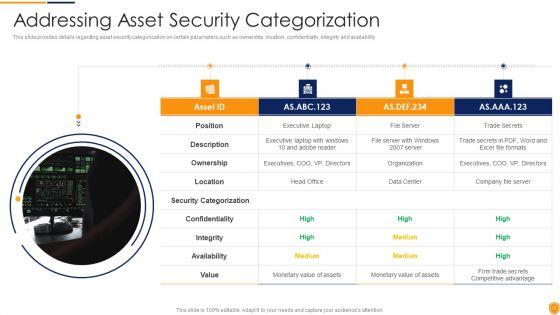
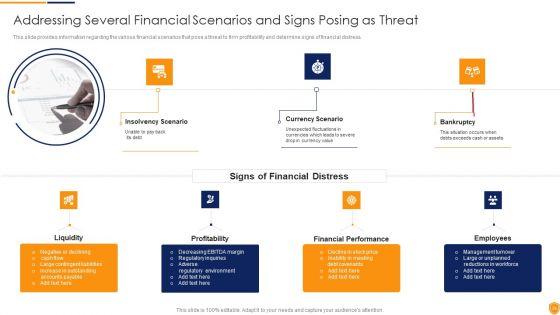
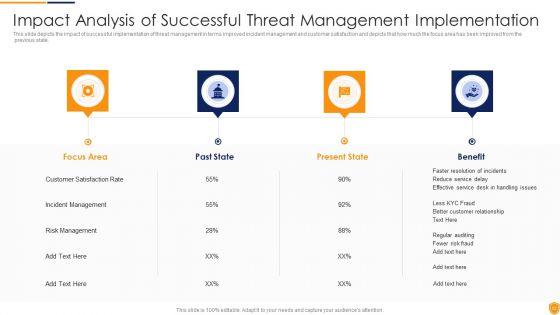
This slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Showcasing this set of slides titled Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF. The topics addressed in these templates are Exposure Score, Configuration Score, Severity Distribution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
This slide defines the dashboard for analyzing the vulnerabilities. It includes information related to the severity and vulnerability age matrix. Showcasing this set of slides titled Administration Plan Dashboard For Vulnerability Analysis Microsoft PDF. The topics addressed in these templates are Total Vulnerabilities, Fixable Vulnerabilitie, Vulnerability Age Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Slide 1 of 2
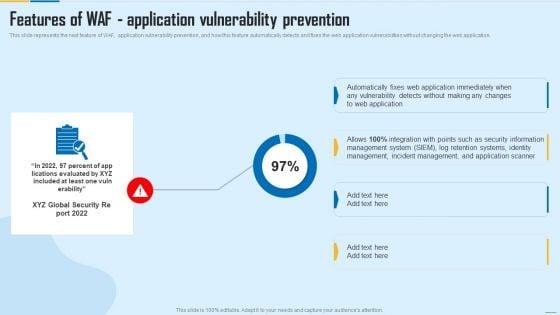
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Deliver and pitch your topic in the best possible manner with this Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF. Use them to share invaluable insights on Management System, Incident Management, Security Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide showcase risk acceptance dashboard with system severity and vulnerability which includes accepted risks by severity, highly severe risks, summarized severity, etc. Showcasing this set of slides titled Risk Management Dashboard With System Severity And Vulnerability Template PDF. The topics addressed in these templates are Risk Management Dashboard, System Severity And Vulnerability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
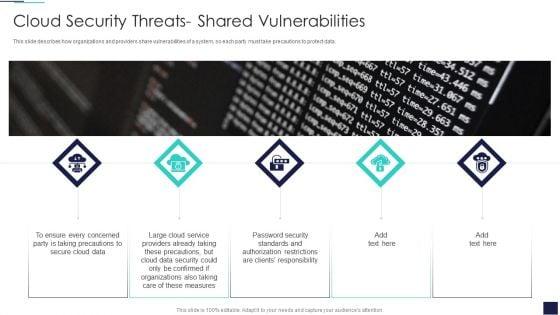
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Security Threats Shared Vulnerabilities Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Could, Organizations, Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
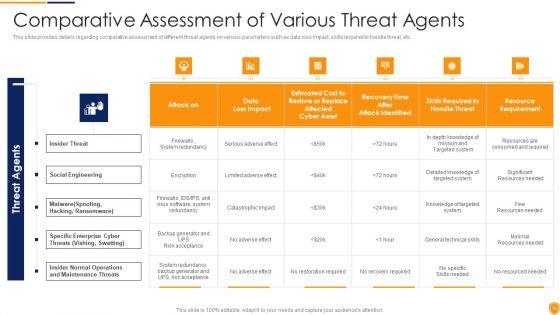
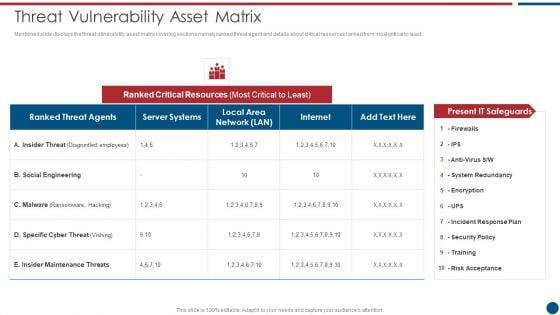
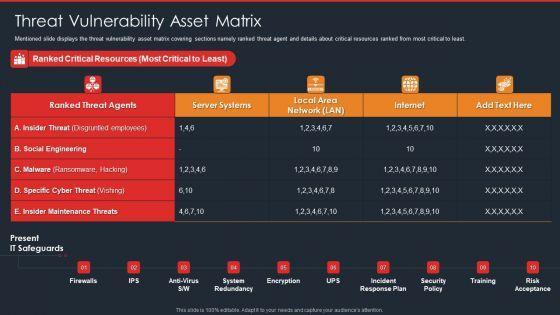
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Information Security Cloud Security Threats Shared Vulnerabilities Ppt File Influencers PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure Cloud, Providers Already, Cloud Service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
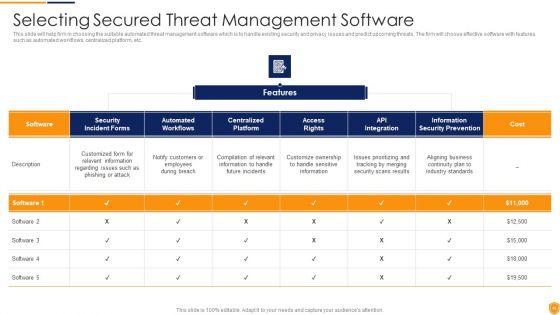
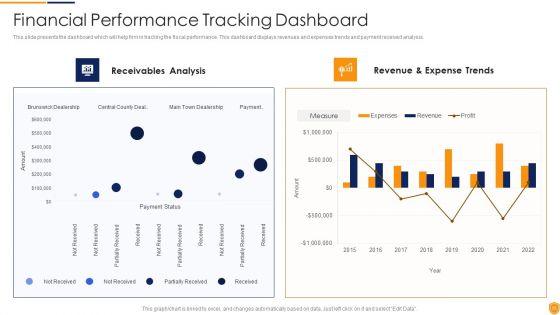
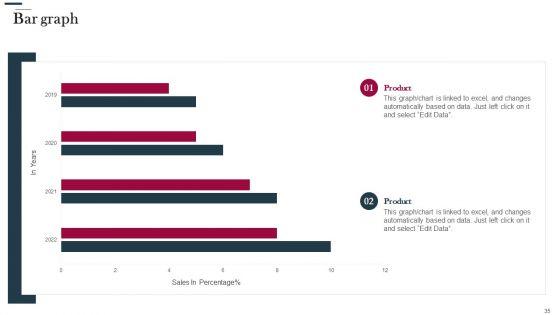
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This slide shows the assessment report prepared through data analytics showing the weaknesses identified in management of supply chain risks. It includes details related to vulnerability comparison to industry benchmark and financial resiliency scores Showcasing this set of slides titled Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF. The topics addressed in these templates are Planning And Supplier Network, Transportation And Logistics, Financial Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
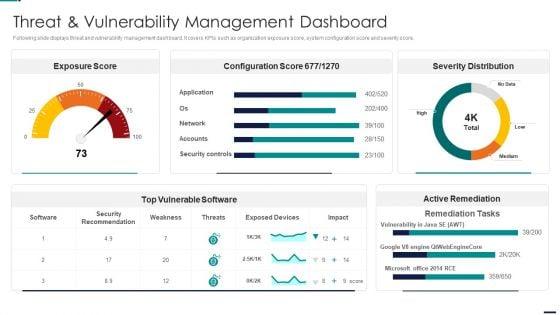
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF Use them to share invaluable insights on Exposure Score, Remediation Tasks, Severity Distribution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
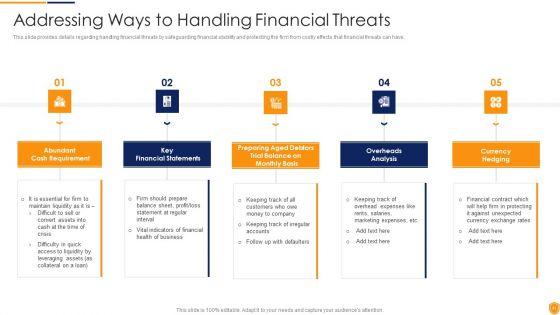
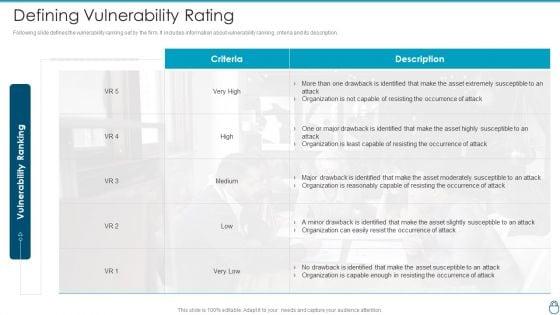
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF Use them to share invaluable insights on Organization Is Not Capable, Resisting The Occurrence Of Attack, Drawback Is Identified and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
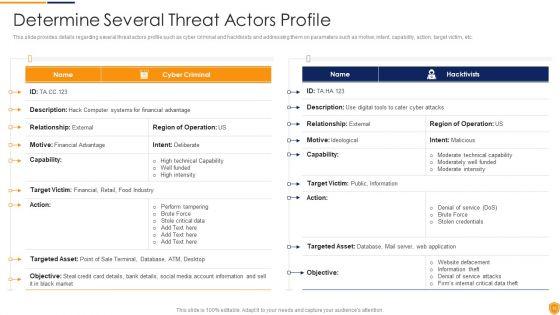
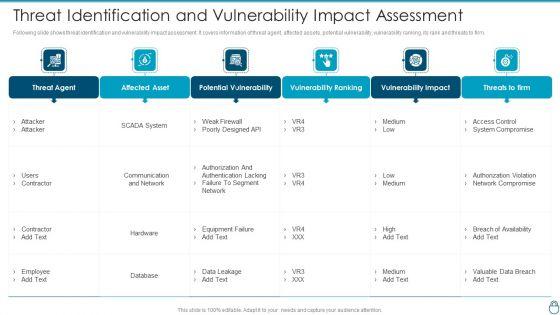
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF bundle. Topics like Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
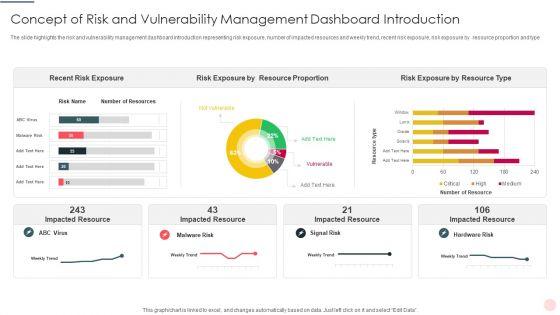
Showcasing this set of slides titled Concept Of Risk And Vulnerability Management Dashboard Introduction Portrait PDF The topics addressed in these templates are Recent Risk Exposure, Risk Exposure, Impacted Resource All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Slide 1 of 2
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF bundle. Topics like Exposure Score, Configuration Score, Severity Distribution, Top Vulnerable Software, Active Remediation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
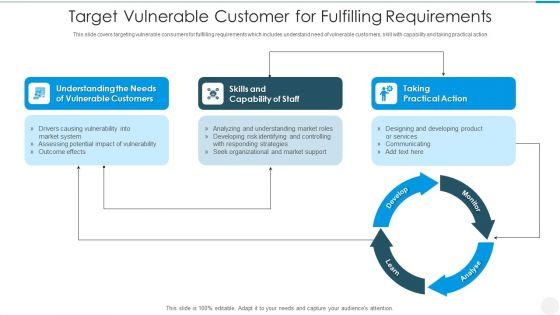
This slide covers targeting vulnerable consumers for fulfilling requirements which includes understand need of vulnerable customers, skill with capability and taking practical action Showcasing this set of slides titled target vulnerable customer for fulfilling requirements designs pdf. The topics addressed in these templates are market system, strategies, organizational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Slide 1 of 2
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this data safety initiatives threat vulnerability asset matrix themes pdf. Use them to share invaluable insights on ranked threat agents, insider threat, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative handling cyber threats digital era threat vulnerability asset matrix ppt gallery templates pdf bundle. Topics like erability asset matrix can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
Presenting table of contents enhancing cyber safety with vulnerability administration portrait pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like company overview, challenges and solutions, services offered, features and benefits, siem architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
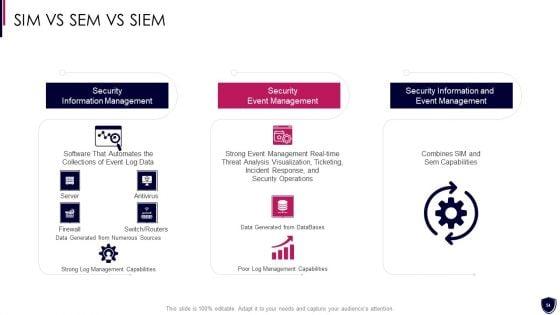
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
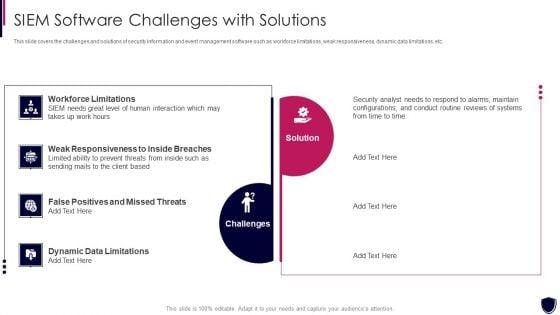
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a enhancing cyber safety with vulnerability administration siem software challenges slides pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like workforce limitations, challenges, solution, weak responsiveness to inside breaches, dynamic data limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting enhancing cyber safety with vulnerability administration siem logging sources microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, network devices, servers, applications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a enhancing cyber safety with vulnerability administration siem integrations inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
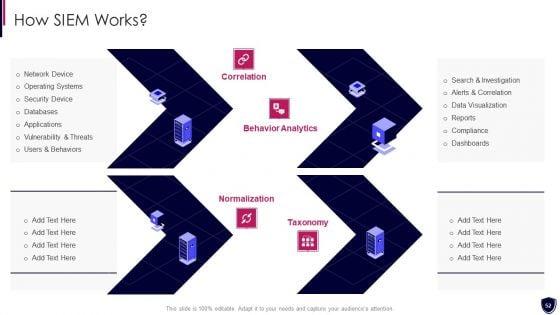
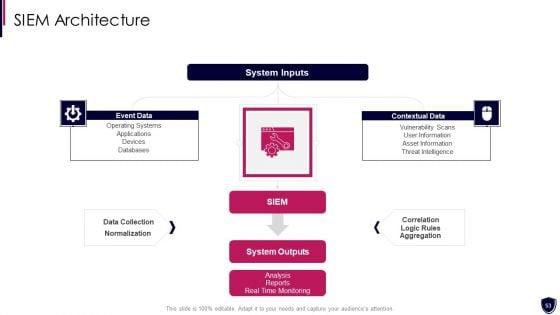
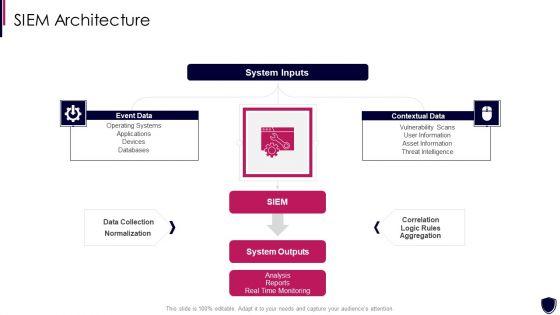
Presenting enhancing cyber safety with vulnerability administration siem architecture information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like event data, contextual data, system inputs, system outputs, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
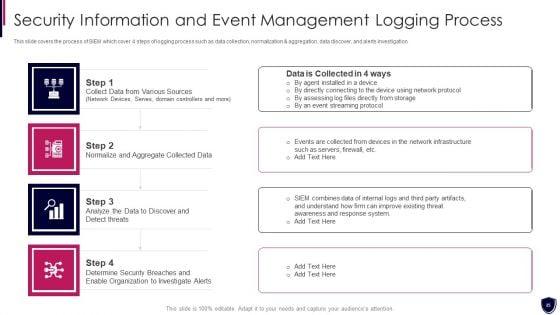
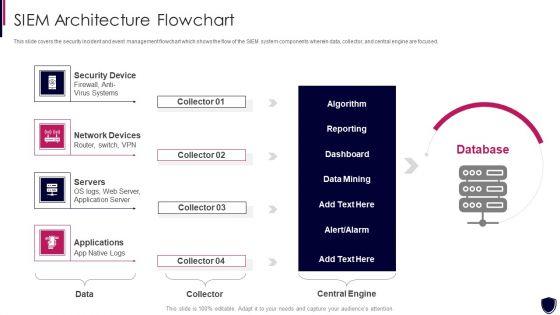
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a enhancing cyber safety with vulnerability administration siem architecture flowchart demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
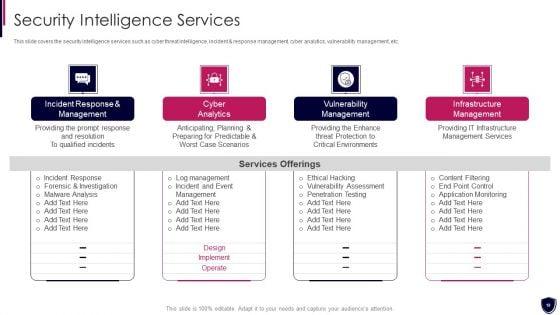
Enhancing Cyber Safety With Vulnerability Administration Security Intelligence Services Portrait PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting enhancing cyber safety with vulnerability administration security intelligence services portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
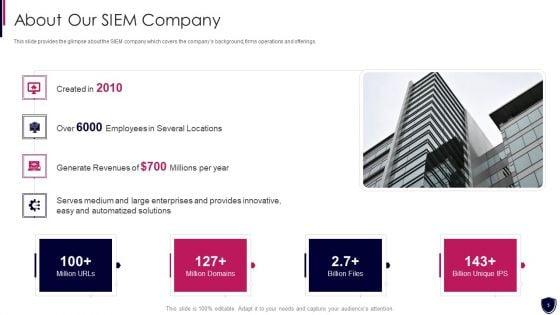
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. This is a enhancing cyber safety with vulnerability administration our siem companys milestones demonstration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our siem companys milestones. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
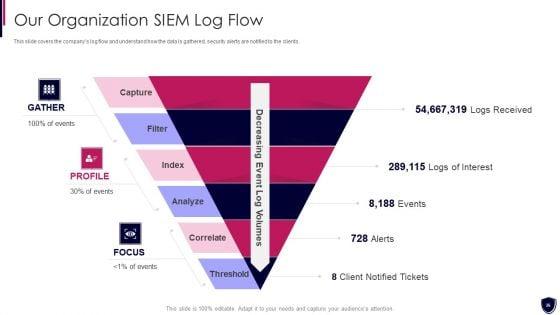
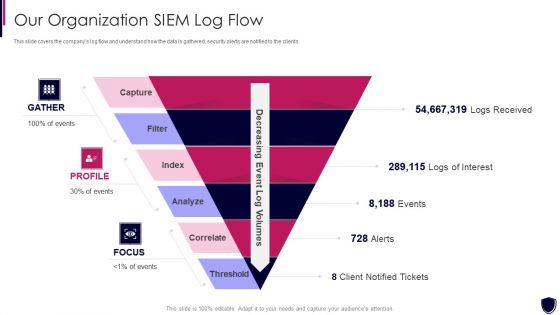
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Presenting enhancing cyber safety with vulnerability administration our organization siem log flow inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like index, analyz, correlate, threshold, capture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
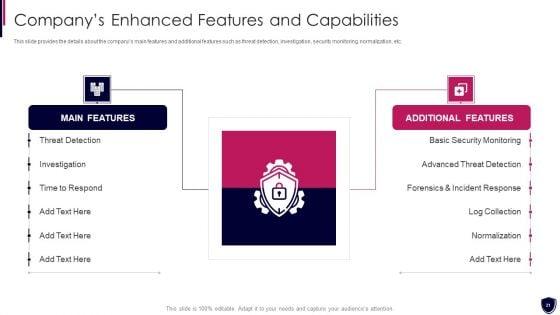
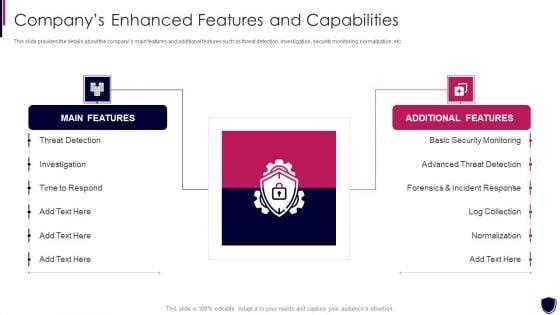
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. This is a enhancing cyber safety with vulnerability administration companys enhanced features download pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like main features, additional features, threat detection, investigation, basic security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
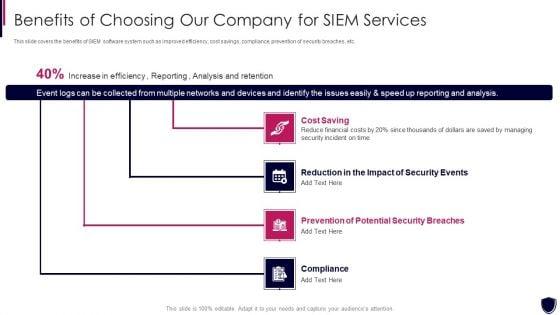
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Slide 1 of 2
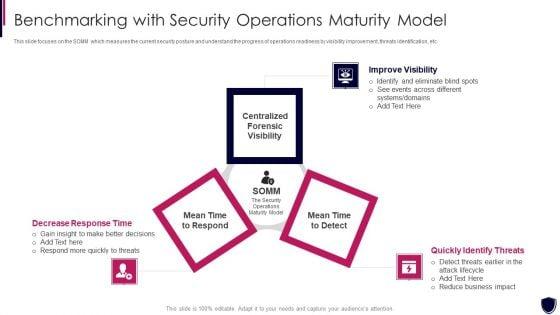
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. This is a enhancing cyber safety with vulnerability administration benchmarking with security inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like improve visibility, quickly identify threats, decrease response time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
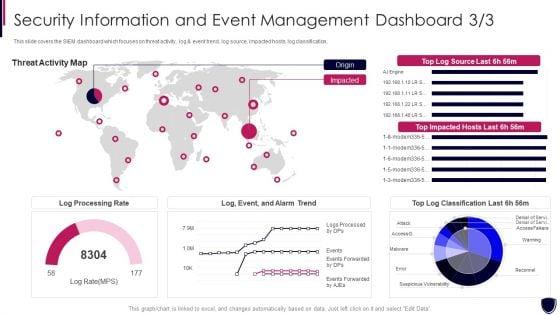

Slide 1 of 2
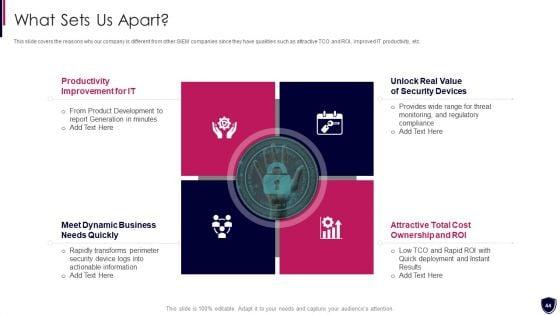
Security Information And Event Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
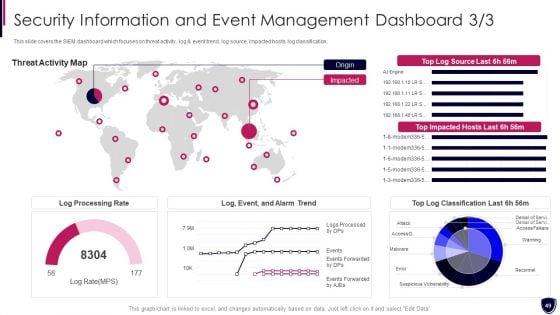
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event enhancing cyber safety with vulnerability administration portrait pdf bundle. Topics like log processing rate, threat activity map can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
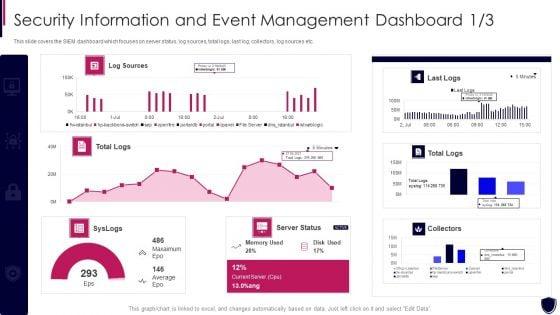

Slide 1 of 2
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this security information and event dashboard enhancing cyber safety with vulnerability administration formats pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
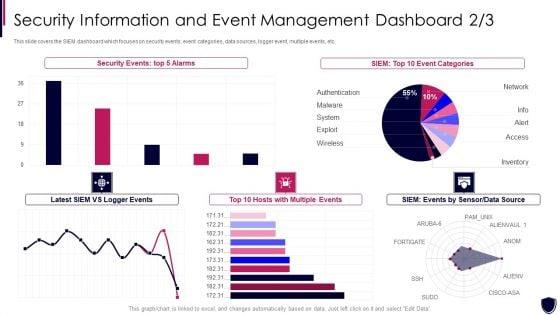

Slide 1 of 2
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration security information and event formats pdf bundle. Topics like security events, event categories, data source, multiple events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
SIEM Competitive Advantage Enhancing Cyber Safety With Vulnerability Administration Introduction PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Deliver and pitch your topic in the best possible manner with this siem competitive advantage enhancing cyber safety with vulnerability administration introduction pdf. Use them to share invaluable insights on security information and event management, application performance monitoring, digital experience management, service health check and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
Download our innovative and attention grabbing icons slide for enhancing cyber safety with vulnerability administration template pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
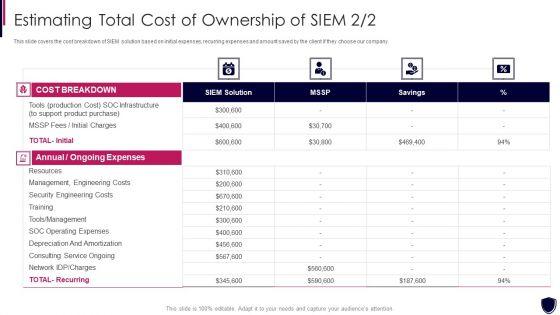
Slide 1 of 2
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver and pitch your topic in the best possible manner with this estimating total cost of ownership enhancing cyber safety with vulnerability administration inspiration pdf. Use them to share invaluable insights on annual and ongoing expenses, cost breakdown, siem solution, security engineering costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration various siem cost plans pictures pdf bundle. Topics like annual costs of tools, annual cost of personnel, one time cost of implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
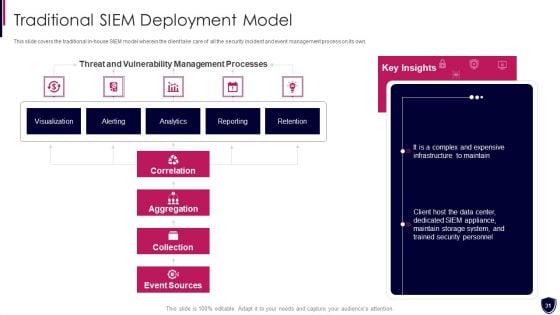
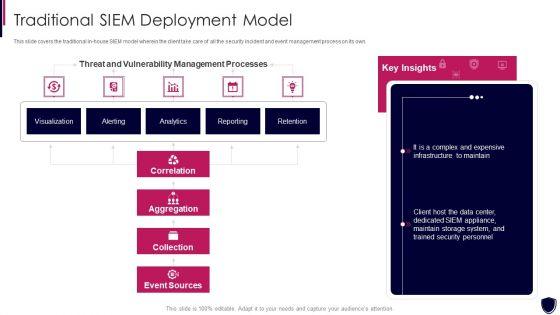
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration traditional siem deployment designs pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
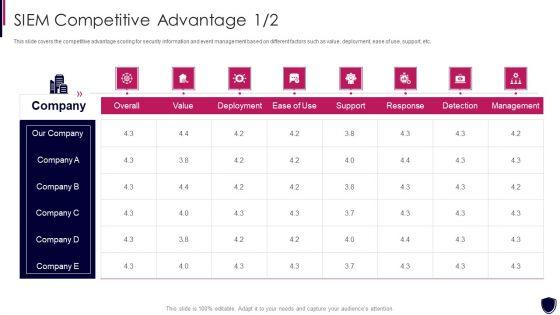

Slide 1 of 2
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration siem competitive advantage designs pdf bundle. Topics like detection, management, deployment, value can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
DISPLAYING: 60 of 374 Item(s)
Page
