AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Vulnerability response PowerPoint Presentation Templates and Google Slides
6 Item(s)

Slide 1 of 2
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This is a company vulnerability administration define the roles and responsibilities designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring roles, remediation roles, authorization roles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
Presenting this set of slides with name vulnerability assessment methodology risk response plan ppt pictures pdf. This is a eight stage process. The stages in this process are exploit, enhance, share, accept, avoid, mitigate, transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 2
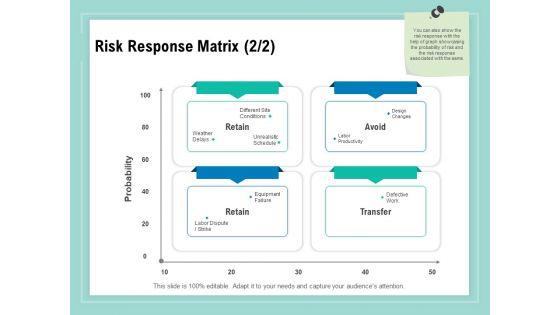
Presenting this set of slides with name vulnerability assessment methodology risk response matrix ppt diagram ppt pdf. This is a four stage process. The stages in this process are retain, avoid, transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.









Slide 1 of 9
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.









Slide 1 of 9
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. This modern and well-arranged Data Breach Response Plan Fix Vulnerabilities Data Breach Prevention Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.
6 Item(s)
