AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Primary approaches PowerPoint Presentation Templates and Google Slides
9 Item(s)


Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this ascertain primary stage for successful application development double diamond approach implementing introduction pdf. Use them to share invaluable insights on develop, communicate, team, techniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This is a ascertain primary stage for successful application development double diamond approach guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing, firm, technology, budget. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Deliver an awe inspiring pitch with this creative ascertain primary stage for successful application development adaptable product discovery approach icons pdf bundle. Topics like optimize, product, process, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Do you have an important presentation coming up Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF today and make your presentation stand out from the rest.









Slide 1 of 9
This slide covers the key attributes of growth marketing strategy to enable marketer to understand and implement. It include elements such as objective, hypothesis, experiment, results and iteration. Make sure to capture your audiences attention in your business displays with our gratis customizable A Comprehensive Approach To Primary Elements Of Growth Marketing MKT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers the key attributes of growth marketing strategy to enable marketer to understand and implement. It include elements such as objective, hypothesis, experiment, results and iteration.









Slide 1 of 9
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
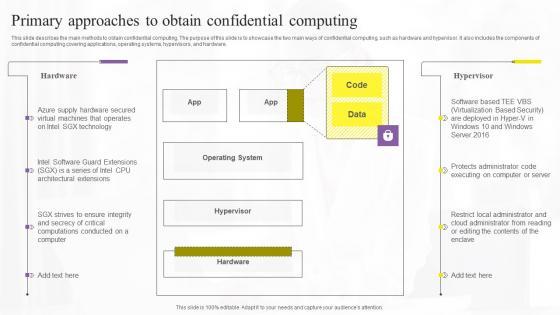








Slide 1 of 9
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.









Slide 1 of 9
This slide represents major types of flippers that serve a valuable function in real estate investing. It covers scouts, dealers and retailers. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Key Primary Classes For Property Flippers Effective Real Estate Flipping Approaches Portrait Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Key Primary Classes For Property Flippers Effective Real Estate Flipping Approaches Portrait Pdf. This slide represents major types of flippers that serve a valuable function in real estate investing. It covers scouts, dealers and retailers.









Slide 1 of 9
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
9 Item(s)
