AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Hashing PowerPoint Presentation Templates and Google Slides
8 Item(s)
Slide 1 of 2
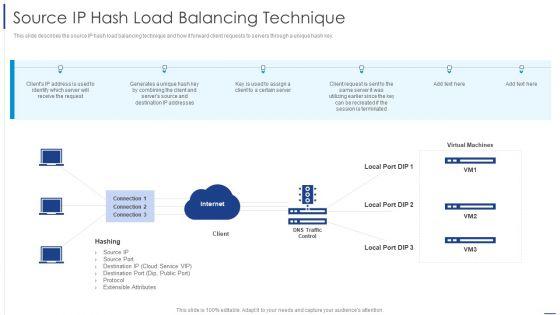
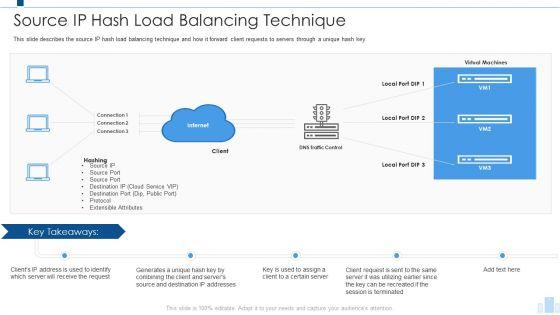
This slide describes the source IP hash load balancing technique and how it forward client requests to servers through a unique hash key. Deliver and pitch your topic in the best possible manner with this Load Balancing Technique Source IP Hash Load Balancing Technique Brochure PDF. Use them to share invaluable insights on Internet, Source Port and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
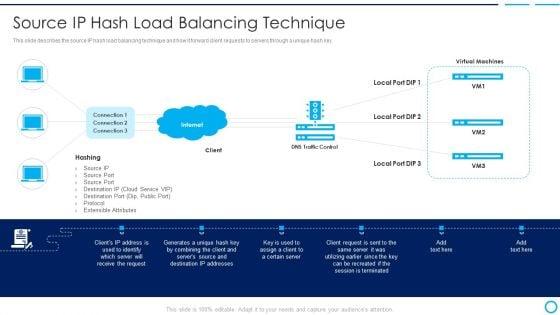
This slide describes the source IP hash load balancing technique and how it forward client requests to servers through a unique hash key. Deliver and pitch your topic in the best possible manner with this categories of load balancer source ip hash load balancing technique brochure pdf. Use them to share invaluable insights on source port, extensible attributes, destination port and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
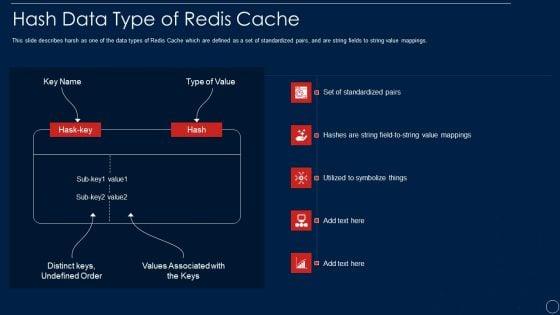
This slide describes harsh as one of the data types of Redis Cache which are defined as a set of standardized pairs, and are string fields to string value mappings. Deliver and pitch your topic in the best possible manner with this redis cache data structure it hash data type of redis cache information pdf. Use them to share invaluable insights on hash data type of redis cache and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
This slide describes the source IP hash load balancing technique and how it forward client requests to servers through a unique hash key. Deliver an awe inspiring pitch with this creative load balancing it source ip hash load balancing technique information pdf bundle. Topics like protocol, service, source can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
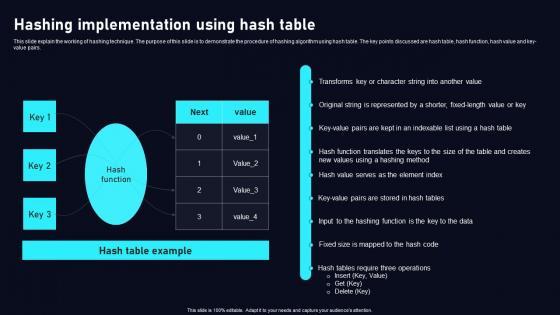
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key-value pairs. Retrieve professionally designed Hashing Implementation Using Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key-value pairs.








Slide 1 of 9
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs. Find a pre designed and impeccable Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs.
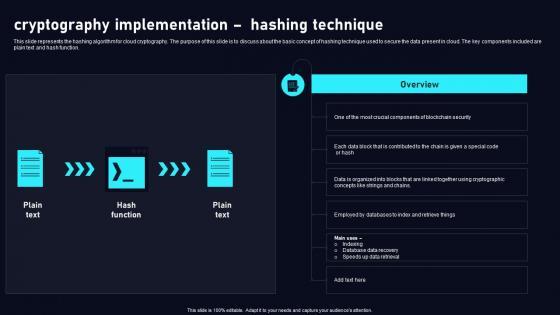








Slide 1 of 9
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
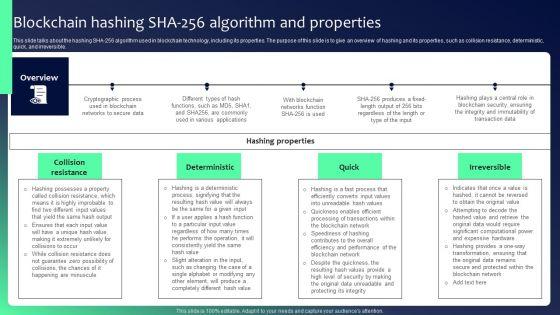








Slide 1 of 9
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
8 Item(s)
