AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Conduct security PowerPoint Presentation Templates and Google Slides
14 Item(s)

Slide 1 of 2
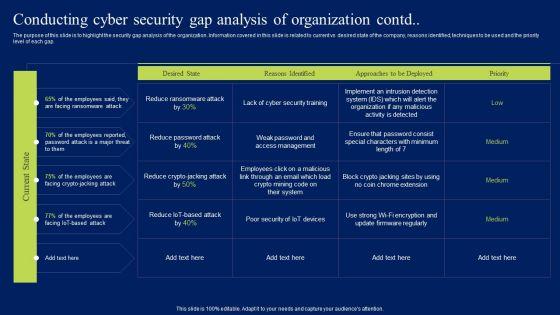
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Boost your pitch with our creative Conducting Cyber Security Gap Analysis Of Organization Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.


Slide 1 of 2
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Slide 1 of 2
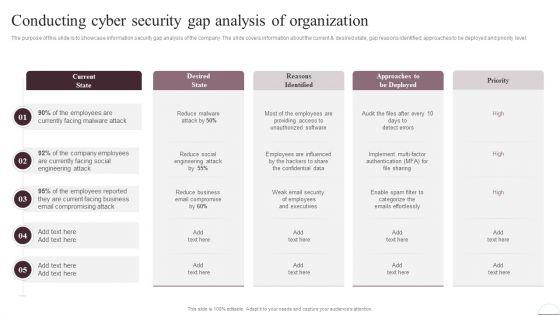
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
Slide 1 of 2
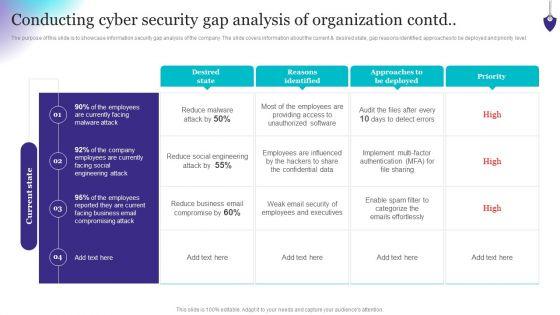
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. There are so many reasons you need a Organizing Security Awareness Conducting Cyber Security Gap Analysis Of Organization Contd Portrait PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

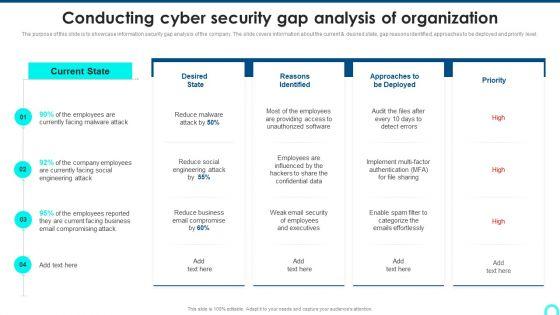
Slide 1 of 2
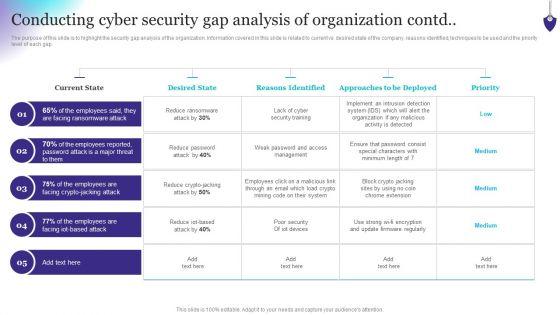
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
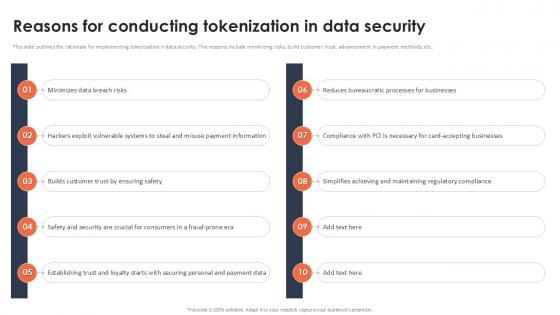
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Boost your pitch with our creative Reasons For Conducting Tokenization In Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
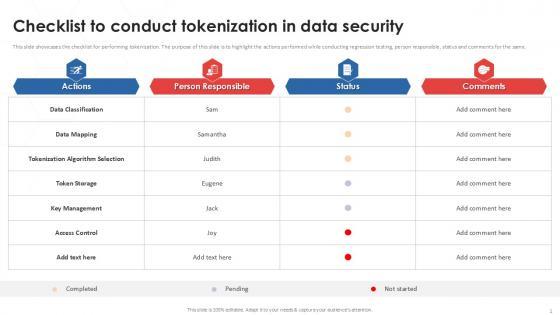








Slide 1 of 9
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Boost your pitch with our creative Checklist To Conduct Tokenization In Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same.









Slide 1 of 9
This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training. If you are looking for a format to display your unique thoughts, then the professionally designed Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training.








Slide 1 of 9
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Do you know about Slidesgeeks Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
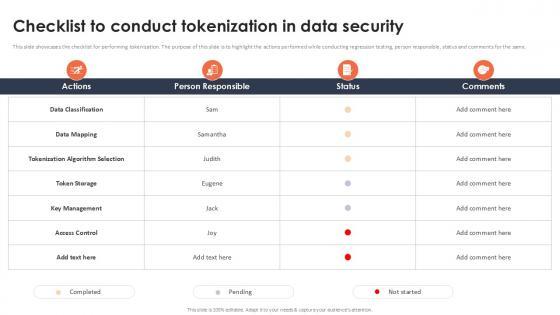








Slide 1 of 9
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present like a pro with Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same.
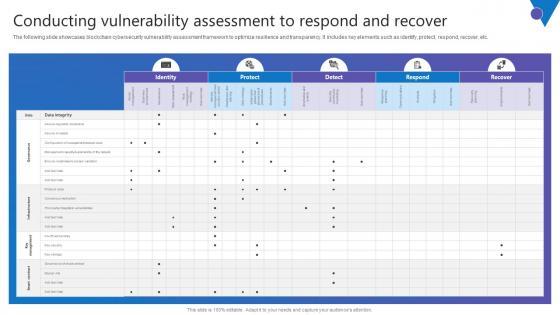








Slide 1 of 9
The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Conducting Vulnerability Comprehensive Guide To Blockchain Digital Security Mockup Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc.
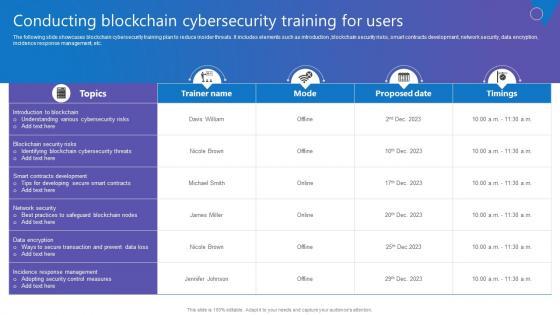








Slide 1 of 9
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc.









Slide 1 of 9
This slide highlights the poor work practices at worksites which showcases defective tools usage, improper lifting, high load at extension cords with general principal for inspections. Find highly impressive Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the poor work practices at worksites which showcases defective tools usage, improper lifting, high load at extension cords with general principal for inspections.
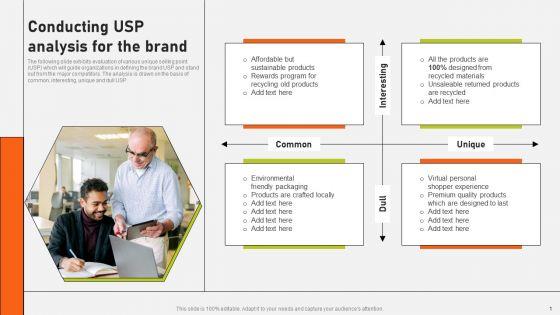








Slide 1 of 9
The following slide exhibits evaluation of various unique selling point USP which will guide organizations in defining the brand USP and stand out from the major competitors. The analysis is drawn on the basis of common, interesting, unique and dull USP. Get a simple yet stunning designed Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
14 Item(s)
