AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
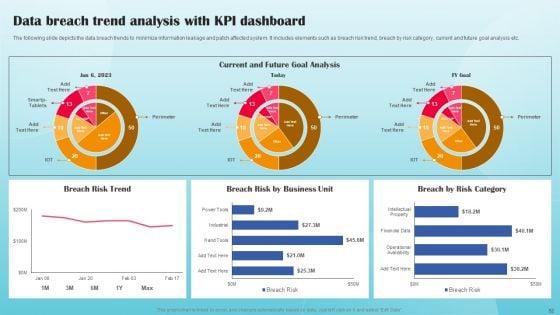
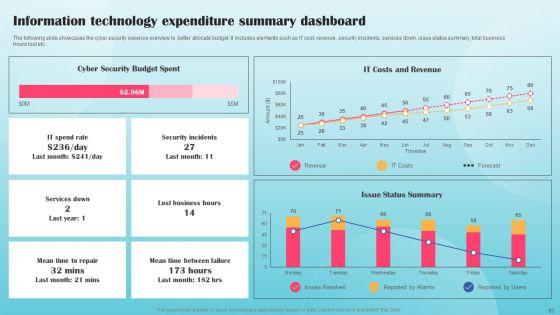
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
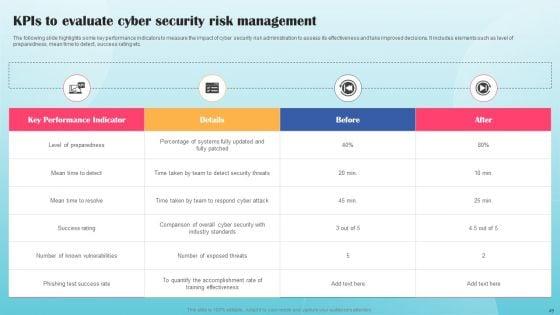
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Building security PowerPoint Presentation Templates and Google Slides
DISPLAYING: 60 of 98 Item(s)
Page














































Slide 1 of 65
Arouses curiosity in the audience is the USP of this Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Ppt PowerPoint Presentation Complete Deck With Slides. The image shown compliments the text provided. The holistic image conveys the message that we are on to something important, the deep world of business communication training. Download it now, and as always customize and edit each of the sixty five slides as per convenience and the data and the experience you are comfortable sharing with your audience.

Slide 1 of 3
Building Financial Security PowerPoint Templates And PowerPoint Themes 1012-We have a piggy bank here that you will just fall in love with. You can use this Template for presentations on money box cash box savings box collecting box. This image has been professionally designed to emphasize the concept of building Financial Security for your Business as well for your Home. Our PPT images are so ideally designed that it reveals the very basis of our PPT Template and are an effective tool to make your clients understand.-Building Financial Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Financial insurance. Piggy bank with padlock, finance, business, money, security, shapes Present like a director with our Building Financial Security PowerPoint Templates And PowerPoint Themes 1012. Make sure your presentation gets the attention it deserves.


Slide 1 of 2
This slide portrays information regarding development of corporate security governance framework including board of directors, senior executives, steering committees in order to ensure the effective corporate security governance. Create an editable Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Slide 1 of 2
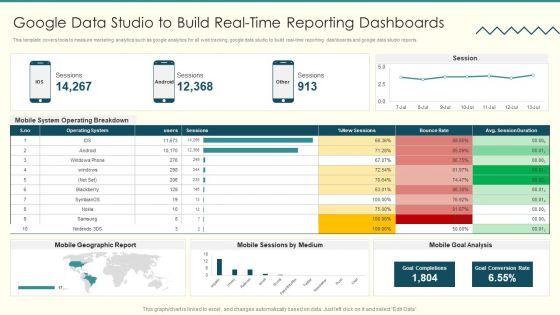
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF bundle. Topics like Operating Breakdown, Session Duration, Goal Completions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
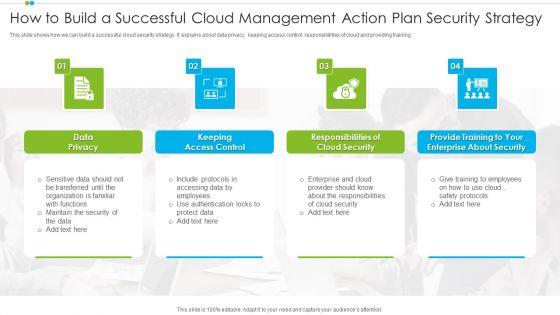

Slide 1 of 2
This slide shows how we can build a successful cloud security strategy. It explains about data privacy, keeping access control, responsibilities of cloud and providing training.Presenting How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Enterprise, Data Privacy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
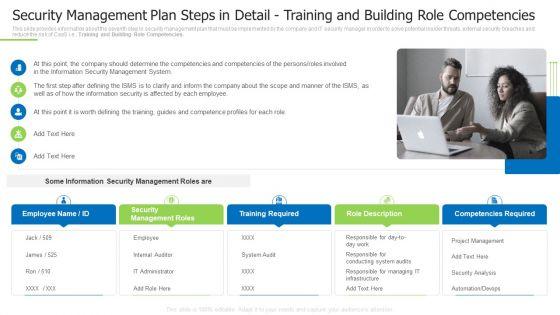
Slide 1 of 2
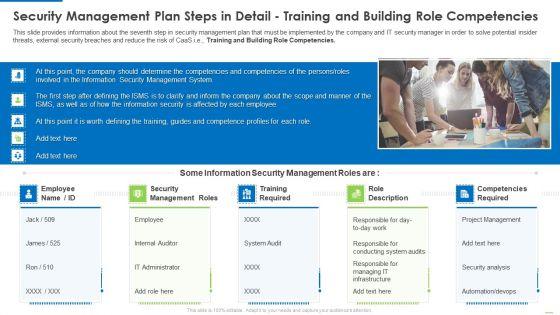
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies slides pdf to provide visual cues and insights. Share and navigate important information on five tages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a security management plan steps in detail training and building role competencies infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsible for conducting, responsible for managing, project management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
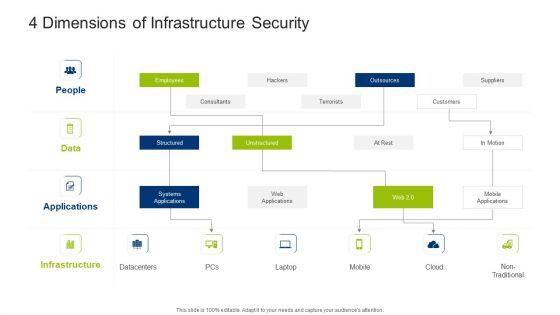
This is a infrastructure building administration interdependence resiliency and security microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this infrastructure building administration 4 dimensions of infrastructure security designs pdf. Use them to share invaluable insights on systems applications, structured, unstructured, employees, outsources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
Presenting security guards standing outside bank building vector icon ppt powerpoint presentation icon files pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including security guards standing outside bank building vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
Showcasing this set of slides titled bank building with cctv cameras for security ppt powerpoint presentation icon background images pdf. The topics addressed in these templates are bank building with cctv cameras for security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Slide 1 of 2
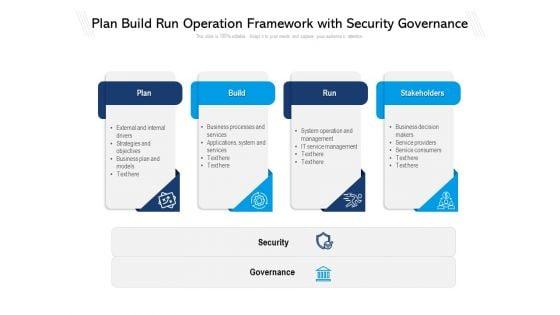
Presenting plan build run operation framework with security governance ppt powerpoint presentation infographics master slide pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Plan, Build, Run, Stakeholders, Security, Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Slide 1 of 2
Pitch your topic with ease and precision using this picture showing security officer in building control room ppt powerpoint presentation file layout ideas pdf. This layout presents information on picture showing security officer in building control room. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Slide 1 of 2
Presenting this set of slides with name building project highlights with safety and security features ppt powerpoint presentation slides display pdf. This is a eleven stage process. The stages in this process are gated community, safety and security features, smartly designed homes, club house and terrace amenities, electricity power backup for common areas, sewage treatment plant, fire safety measures and installations, water backup, energy efficient lights in common area. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
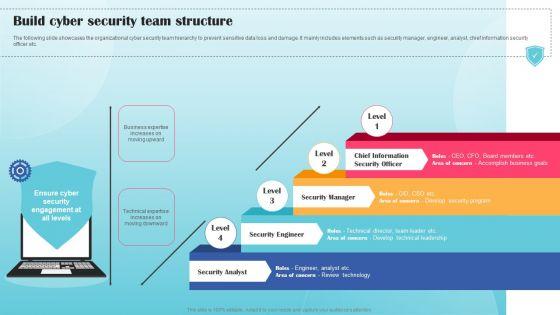








Slide 1 of 9
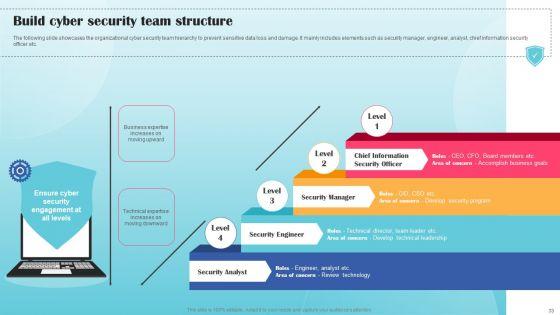
The following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates









Slide 1 of 9
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.








Slide 1 of 9
Introducing our well designed Icons Slide Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.









Slide 1 of 9
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.









Slide 1 of 9
Find a pre designed and impeccable Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.








Slide 1 of 9
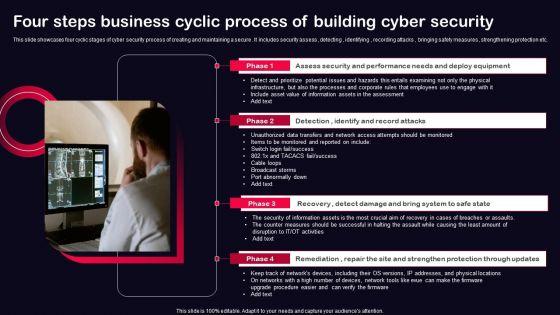
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.








Slide 1 of 9
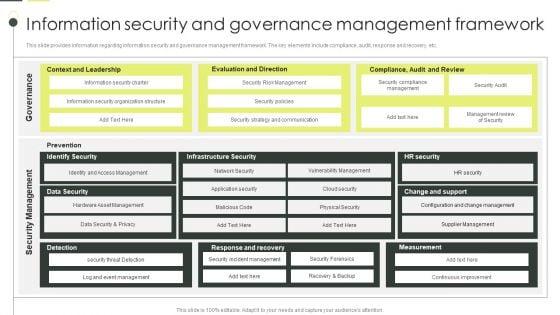
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Building An IT Strategy Plan For Business Expansion Information Security And Governance Management Framework Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Building An IT Strategy Plan For Business Expansion Information Security And Governance Management Framework Background PDF today and make your presentation stand out from the rest.









Slide 1 of 9
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. There are so many reasons you need a Building An IT Strategy Plan For Business Expansion Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.








Slide 1 of 9
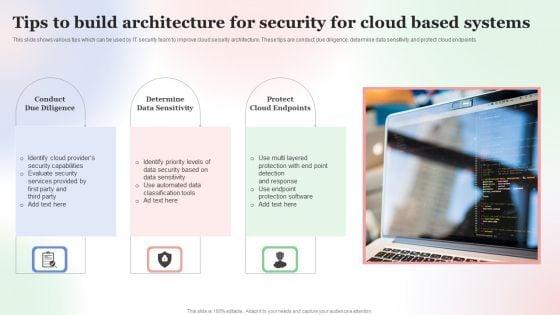
This slide shows various tips which can be used by IT security team to improve cloud security architecture. These tips are conduct due diligence, determine data sensitivity and protect cloud endpoints. Persuade your audience using this Tips To Build Architecture For Security For Cloud Based Systems Designs PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Tips To Build, Architecture For Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.








Slide 1 of 9
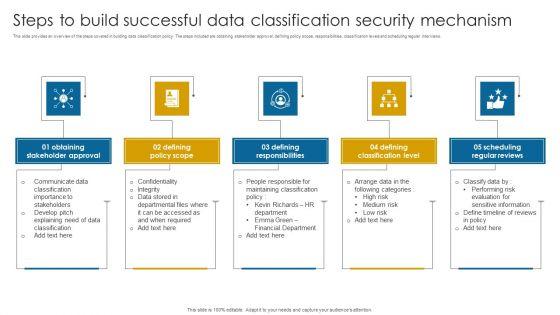
This slide provides an overview of the steps covered in building data classification policy. The steps included are obtaining stakeholder approval, defining policy scope, responsibilities, classification levels and scheduling regular interviews.Presenting Steps To Build Successful Data Classification Security Mechanism Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Stakeholder Approval, Defining Policy Scope, Defining Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
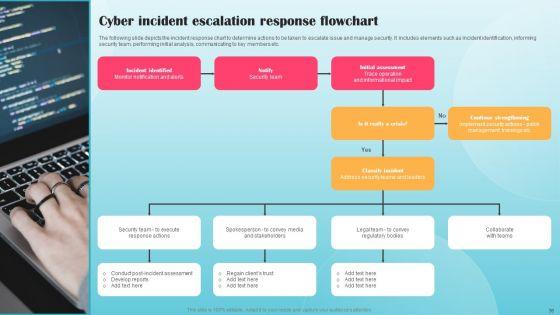
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
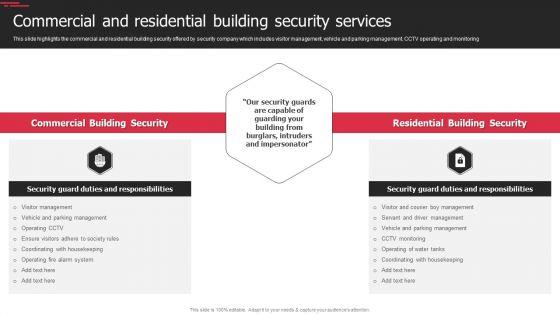
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.








Slide 1 of 9
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.








Slide 1 of 9
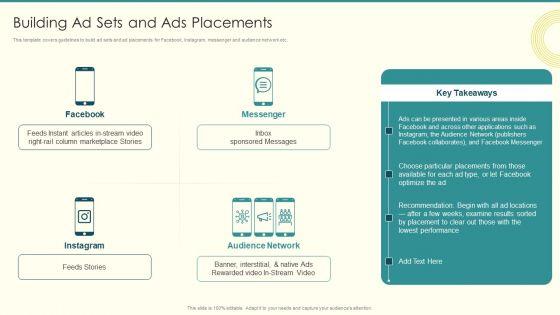
This template covers guidelines to build ad sets and ad placements for Facebook, Instagram, messenger and audience network etc. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF. Use them to share invaluable insights on Column Marketplace, Presented Various, Choose Particular and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.









Slide 1 of 9
This template covers the goal of profiling accounts, such as determining an accurate value proposition for each account. It also depicts that to get the compelling value proposition, companies have to research the role of the target and examine the targets perspective.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Build Personas And Value Props For The Targets Brochure PDF bundle. Topics like Value Proposition, Business Channels, Purchasing Characteristics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.








Slide 1 of 9
This slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Persuade your audience using this Building Data Analytics And Cyber Security Strategy Framework Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Expansion, Standardize And Automate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.








Slide 1 of 9
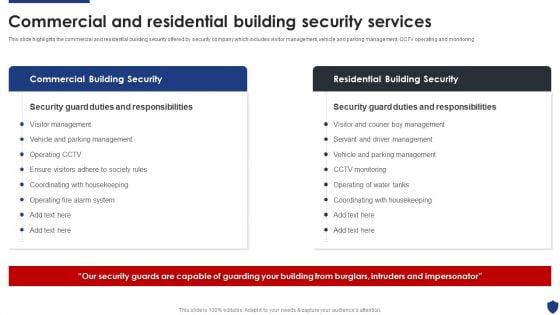
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF bundle. Topics like Commercial Building Security, Residential Building Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.









Slide 1 of 9
This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc.








Slide 1 of 9
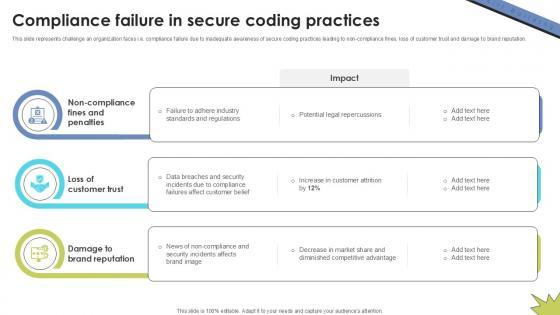
This slide represents challenge an organization faces i.e. compliance failure due to inadequate awareness of secure coding practices leading to non-compliance fines, loss of customer trust and damage to brand reputation. Want to ace your presentation in front of a live audience Our Compliance Failure In Secure Skill Building Plan For Application PPT Slide DTE SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents challenge an organization faces i.e. compliance failure due to inadequate awareness of secure coding practices leading to non-compliance fines, loss of customer trust and damage to brand reputation.










Slide 1 of 10
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Our Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.









Slide 1 of 9
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.








Slide 1 of 9
If you are looking for a format to display your unique thoughts, then the professionally designed Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.









Slide 1 of 9
This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware.








Slide 1 of 9
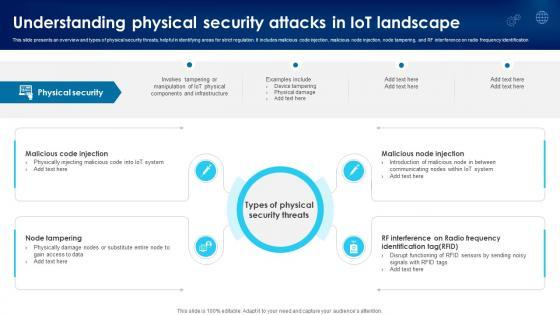
This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification. Find highly impressive Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification.









Slide 1 of 9
This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks.








Slide 1 of 9
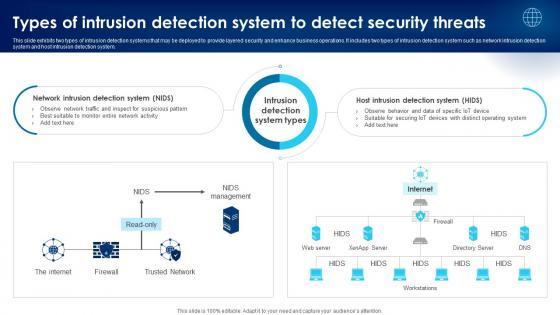
This slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Building Trust With IoT Security Types Of Intrusion Detection System To Detect Security Threats IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Building Trust With IoT Security Types Of Intrusion Detection System To Detect Security Threats IoT SS V today and make your presentation stand out from the rest This slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system.








Slide 1 of 9
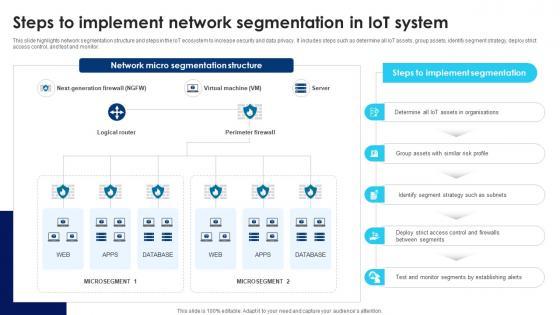
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.








Slide 1 of 9
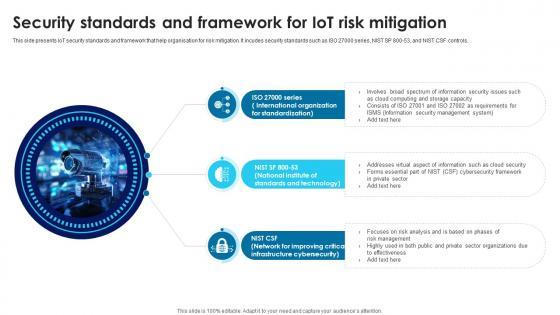
This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls. Present like a pro with Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls.








Slide 1 of 9
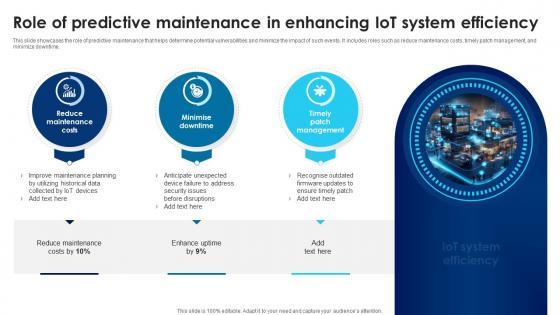
This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime.









Slide 1 of 9
This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact. Get a simple yet stunning designed Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Real Life Examples Of IoT Security Breaches Incident With Impact IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits real-life examples of IoT security breaches and their potential consequences including Mirai botnet, Stuxnet, and Jeep Cherokee hack. It includes elements such as security attack, year of occurrence, targeted device, attack method, and impact.









Slide 1 of 9
This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc.








Slide 1 of 9
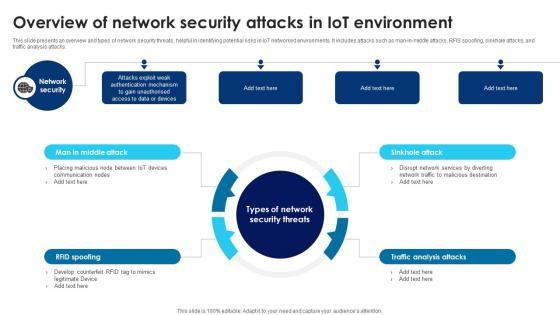
This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. There are so many reasons you need a Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks.








Slide 1 of 9
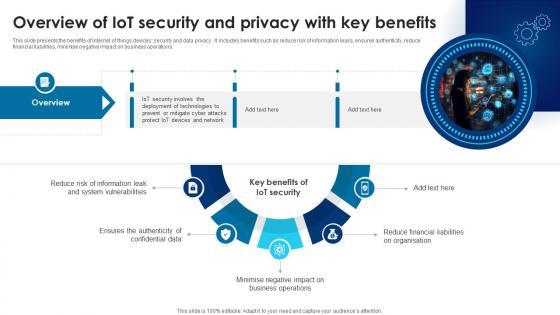
This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations.









Slide 1 of 9
Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack.








Slide 1 of 9
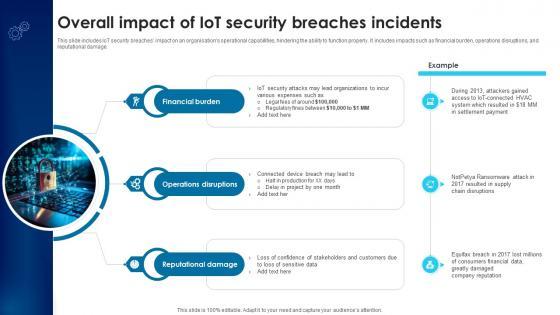
This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage. Create an editable Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage.








Slide 1 of 9
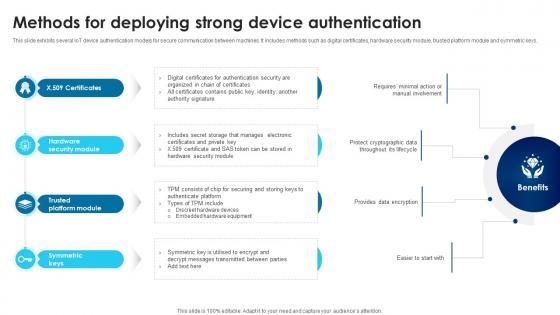
This slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Boost your pitch with our creative Building Trust With IoT Security Methods For Deploying Strong Device Authentication IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys.










Slide 1 of 10
This slide showcases year on year growth of connected devices globally. It includes stats data related to connected devise growth, sensors and actuators market size, and China as a largest contributor to consumer IoT devices. Find a pre-designed and impeccable Building Trust With IoT Security Key Stats Associated With Connected Devices IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases year on year growth of connected devices globally. It includes stats data related to connected devise growth, sensors and actuators market size, and China as a largest contributor to consumer IoT devices.









Slide 1 of 9
This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity. Do you know about Slidesgeeks Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity.









Slide 1 of 9
This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security. Take your projects to the next level with our ultimate collection of Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security.









Slide 1 of 9
This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc. This Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc.








Slide 1 of 9
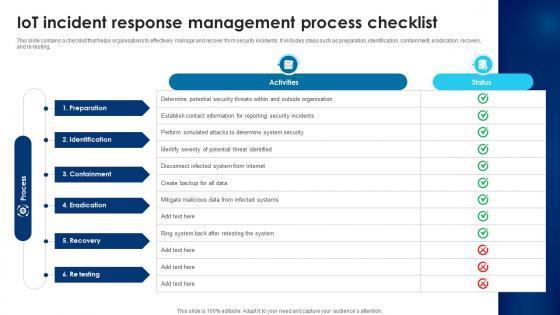
This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V. This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing.
DISPLAYING: 60 of 98 Item(s)
Page
