AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
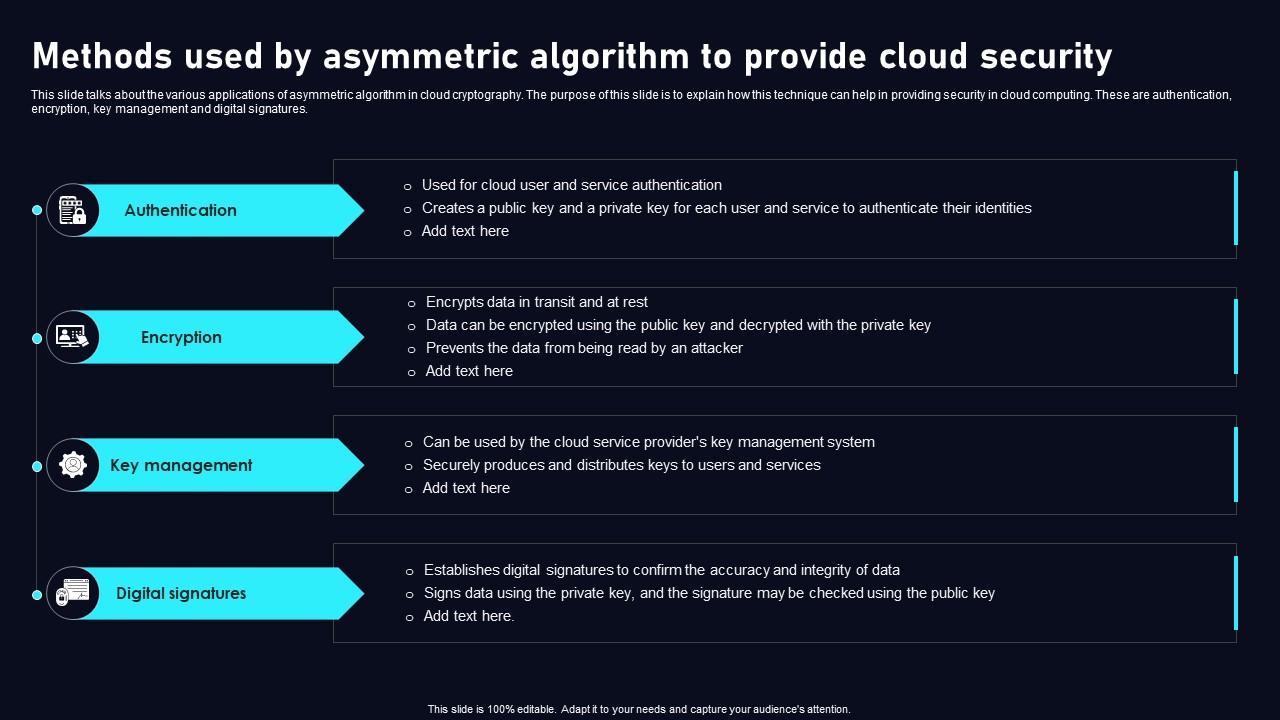
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
Features of these PowerPoint presentation slides:
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Ratings and Reviews
5
- ★54
- ★40
- ★30
- ★20
- ★10
Write a review
Most Relevant Reviews
by Cornelius Alexander
February 27, 2024
Perfect template with attractive color combination.by Dalton Aguilar
February 27, 2024
Perfect template with attractive color combination.by Daren Henry
February 27, 2024
Designs have enough space to add content.by Derick Meyer
February 27, 2024
Appreciate the research and its presentable format.
View per page:
10